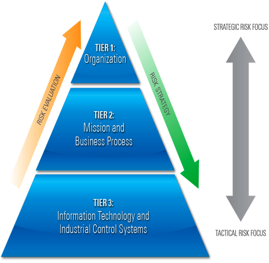
Cybersecurity is integral to all CIP sectors and all levels of an organization. Security is a global problem that permeates across all layers of an organization and impacts each successive layer both upward and downward. This Cyber ERM workshop covers GAO, DOD, DHS, DOE, and NIST high level risk frameworks, models, and taxonomies (Tier 1). It will also address the three levels of the risk NIST RMF in terms of alignment, purpose, process, risk, and controls (see NIST 800-37 figure) and the Federal Enterprise Architecture Framework Ver. 2.
 This workshop helps participants understand the benefits of a holistic cyber governance approach, develop cyber enterprise risk management skills, and apply what they learned to real-life CIP cyber projects. Participants will learn how to implement enterprise cyber risk management in their organizations. Participants will learn why boards and executive management are adopting and developing a portfolio view of cyber risk-controls within their organizations and into the ICT supply stream (NIST IR 7622, NIST SP 161).
This workshop helps participants understand the benefits of a holistic cyber governance approach, develop cyber enterprise risk management skills, and apply what they learned to real-life CIP cyber projects. Participants will learn how to implement enterprise cyber risk management in their organizations. Participants will learn why boards and executive management are adopting and developing a portfolio view of cyber risk-controls within their organizations and into the ICT supply stream (NIST IR 7622, NIST SP 161).
Learning Objectives:
- Understand cyber drivers and reporting requirements, such as SEC, DHS, OMB, etc.
- Understand security architecture and ERM and when to use them.
- Know how to implement security architecture and ERM successfully in different organizations including using NIST 800-37.
- Know high-level security risk taxonomies, such as NIST RMF, COBIT, NIST 800-37 and NIST 53, ISO 27001, etc. risk management frameworks and standards.
- Identify enterprise risk tolerance for operational and supply chain risk decision making (NIST IR 7622).
- Apply the cyber enterprise risk management and assessment process.
- Apply cyber risk principles: identification, assessment, mitigation, tracking, and monitoring practices.
- Apply NIST RMF and ERM cyber security controls to mitigate cyber risks, threats, and vulnerabilities.
Workshop Outline:
- Statutory and Business Drivers for Cyber Enterprise Risk Management.
- Introduction to ERM and NIST Cyber Risk Frameworks (800-37, 800-53, etc.)
- Department of Energy (DOE) Risk Framework and NIST RMF.
- ICT Supply Risk Management Approach, SDLC, and ERM
- Balancing Enterprise Confidentiality, Integrity, and Availability.
- Cyber Control Architecture (Policies, Procedures, Instructions, Standards).
- Introduction Cyber Process Management.
- Primary Enterprise Threats and Vulnerabilities Based on Existing Business Model.
- How to Cyber Design Compliance for Different Architectural Layers.
- Identify Enterprise, Process, and System Cyber Risk Appetites, Tolerances, and Assurance.
- Cyber Risk Management: Risk Assessment Techniques – Quantitative & Qualitative.
- Cyber Enterprise Control Design, Deployment, Enforcement, and Assurance.
- Cyber Enterprise Risk Management: Risk Control, Mitigation Strategies and Techniques.
- ERM Cyber Reporting: To Whom And What Information.
